It did not take much for Russian hacker groups to wreak havoc on Democratic presidential nominee Hillary Clinton and the Democratic Party. In fact, it was as easy as stealing a few passwords.
Russian hacker group “Cozy Bear” first penetrated the computer networks of the Democratic National Committee (DNC) in the summer of 2015. The hackers were able to gain access to the DNC by exploiting what is known in the computer programming world as a “back door,” or computer code that allows an administrator (or hacker) to bypass a computer program’s security features. Some back doors are created intentionally, whereas Cozy Bear’s was injected into the server.
Once inside the DNC’s computer networks, Cozy Bear had access to the organization’s deepest, darkest secrets.
The DNC was hacked again in April 2016, this time by a different Russian hacking outfit known as Fancy Bear. The group’s tactics differed from Cozy Bear. Instead of manipulating a back door, Fancy Bear used a malware program called an “X Agent” to breach the servers. X Agents collect and transmit information from iPhones and send it to the hacker using what is known as a “spear phishing” attack. Spear phishing is a simple hacker tactic which involves convincing a target to unwittingly provide their user credentials and passwords, generally through a fake email from a trusted source.
The X Agent used by Fancy Bear to breach the DNC was even more sophisticated. It gave the hackers the ability to send remote commands to the DNC network, recorded key strokes by those using it and transferred information remotely back to Fancy Bear’s servers. Fancy Bear even deployed a program that covered up evidence it was inside the servers.
DNC workers first noticed signs of a breach in June, around the same time opposition research by the DNC on current Republican presidential nominee Donald Trump was leaked. The DNC soon discovered it had been hacked, but it was too late.
The DNC hired Crowdstrike, a cyber security firm, to investigate the breach. Crowdstrike’s Incident Response group examined the tools, tactics and locations of the hackers and quickly realized they were dealing with an old adversary.
“We deployed our IR team and technology and immediately identified two sophisticated adversaries on the network — Cozy Bear and Fancy Bear,” said Dmitri Alperovitch, co-founder and CTO of Crowdstrike, in a blog post. “We’ve had lots of experience with both of these actors attempting to target our customers in the past and know them well.”
Cozy Bear, also known as CozyDuke or APT 29, previously hacked the White House, the Department of State and the Joint Chiefs of Staff. It also regularly targets non-governmental institutions across multiple sectors, ranging from the defense industry to universities. It specializes in spear phishing campaigns that cause a target to download sophisticated malware giving hackers remote access to a computer or server. Crowdstrike believes Cozy Bear has links to Russia’s Federal Security Service (FSB), but it is not completely sure of its exact origins.
Fancy Bear, also known as Sofacy or APT 28, has been operating since the mid 2000s. Crowdstrike believes the group is tied to GRU, Russia’s main military intelligence branch, given its target profile. That said, Fancy Bear is completely separate from Cozy Bear. In fact, Alperovitch noted that his team found no evidence of the two groups coordinating whatsoever. They likely were not even aware that they both were in the DNC servers at the same time.
While it may seem strange that Russia would have two hacker groups operating independent of each other, the strategy actually follows Russian intelligence trade craft which emphasizes using competing intelligence agencies.
While Fancy Bear’s targets are similar to those of Cozy Bear, its tactics are different. The group specializes in the registration of website domain names that appear similar to popular, well-known websites. Fancy Bear then sends out spear phishing emails which direct targets to input their log-in information on the fake sites, thus giving them access to the targets online accounts. This was the exact tactic the group used to break into the email account of Clinton campaign chairman John Podesta.
ThreatConnect, a cyber security firm which follows Fancy Bear’s spear phishing campaigns, caught the group trying to use the same strategy it used with Podesta against investigative journalist group Bellingcat.
Bellingcat’s Eliot Higgins, Aric Toler and Veli-Peki Kivimaki were targeted with spear phishing emails from Feb. 2015 to July 2016. The group is known for its investigative work exposing Russia’s connections to the downing of flight MH17 over Ukraine, drawing ire from Russia and Kremlin sympathizers.
Fancy Bear attempted to steal Bellingcat’s accounts by sending fake Gmail security notices to the journalists, prompting them to click a link.
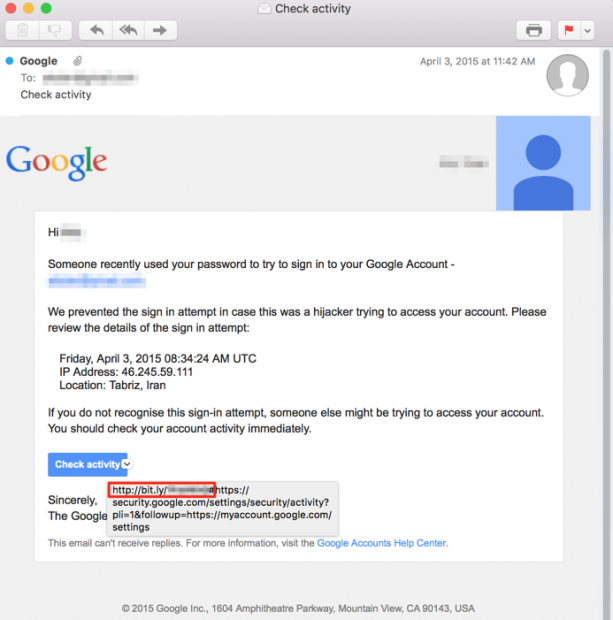
A fake email sent by hacker group Fancy Bear to Bellingcat. Source: courtesy of ThreatConnect
The fake emails appeared remarkably legitimate, but the included links were strange. They were shortened using the online link-shortening service Bitly, which is not normally used by Google in official correspondence.
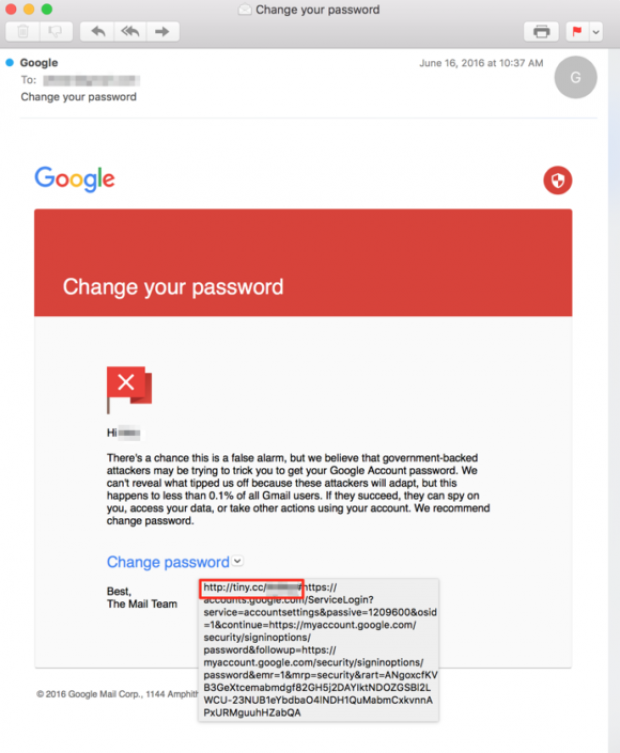
A fake email sent to Bellingcat from hacker group Fancy Bear. Source: courtesy of ThreatConnect
Fancy Bear frequently uses Bitly in their phishing attacks, including the DNC hack. Cyber-security firm Secure Works traced the links sent to DNC staffers back to Bitly profiles owned by Fancy Bear hackers.
Despite thorough evidence pointing to Fancy Bear and Cozy Bear’s involvement in the hacks against Clinton and the Democratic Party, it is the mysterious hacker persona known as Guccifer 2.0 who took credit.
Guccifer 2.0 was offended by Crowdstrike’s assessment, claiming sole responsibility for the DNC breach in June. The persona then began publishing documents stolen from the hack regularly on its website.
The most damning Guccifer 2.0 attack occurred July 22, when WikiLeaks published nearly 20,000 DNC emails on its website. The emails revealed, among other things, that leaders within the DNC were colluding against former Democratic presidential candidate Sen. Bernie Sanders, prompting the resignation of DNC Chair Rep. Debbie Wasserman Schultz.
WikiLeaks claimed Guccifer 2.0 provided the emails, but it is more likely that Guccifer 2.0 does not even exist.
ThreatConnect believes the Guccifer 2.0 persona is nothing more than a mouthpiece through which Fancy Bear spreads hacked information. The company bases its claim on several inconsistencies in Guccifer 2.0’s alleged background.
The cyber-security firm also believes DC Leaks, a website allegedly run by American hackers, is likely nothing more than a Fancy Bear front.
“It turns out that DC Leaks, the domain (website) itself, was registered through a small registrar operating out of Romania,” Kyle Ehmke, a senior analyst at ThreatConnect, told The Daily Caller News Foundation. Known as THC servers, Ehmke noted the company has “previously been used to register domains that have been attributed to other Fancy Bear activity.”
Ehmke also noticed that, like Guccifer 2.0, there are inconsistencies pointing to DC Leaks not being what it claims. Specifically, he noted that the web profiles on the group’s targets includes language borrowed directly from Wikipedia, suggesting English is not the group’s first language. Between the language issue and the use of a relatively unknown hosting company in Europe, the idea that DC Leaks is American based is “suspect,” according to Ehmke.
The hacker groups and the publication fronts essentially operate like an assembly line, with Fancy Bear and Cozy Bear engaging in the operations and various “mouthpieces” pushing the results. Some of those mouthpieces are likely directly tied to the hacker groups, like Guccifer 2.0 and DC Leaks, while others like WikiLeaks are convenient allies.
WikiLeaks published 21 batches of Podesta emails as of the writing of this article, and does not appear to be slowing down any time soon. Given the sophisticated nature of the Russian hacking groups and the deteriorating relations between Russia and the U.S., it is likely the hacks will continue.
Note: a previous version of this article attributed the Podesta leaks to DC Leaks, when they were actually released by WikiLeaks.
Send tips to russ@dailycallernewsfoundation.org.
All content created by the Daily Caller News Foundation, an independent and nonpartisan newswire service, is available without charge to any legitimate news publisher that can provide a large audience. All republished articles must include our logo, our reporter’s byline and their DCNF affiliation. For any questions about our guidelines or partnering with us, please contact licensing@dailycallernewsfoundation.org.


